Commercial Password Management solutions are often relatively expensive and not the most flexible when it comes to various configuration elements such as what text to display, what workflows to follow and how to integrate with other applications and directories that require password synchronization. Additionally, we often encounter many of our customers that have built their own solutions which are often written in ancient programming languages or have become difficult to support and maintain. Fortunately, we have a cost-effective, low maintenance solution, PWM. Password Manager (PWM) is the Open Source product of OpenText SSPR, formerly Micro Focus or NetIQ. Its an actively maintained project on GitHub that has been in existence for many years. There is also a very active community of users on Google Groups.
PWM is essentially a zero-code application that can be deployed using containers or a Tomcat application server. The product requires very little resources, most of our typical installations are 2-CPU with 4GB RAM. Once you deploy the application and setup an environment variable you are on your way to configuring the application through a wizard. All configuration is stored in one single PwmConfiguration.xml file and is also backed up each time you make a change, allowing for very simple roll-back operations. The product comes with several built-in themes, however with some basic CSS skills you can create your own look and feel and upload a ZIP file of your images, fonts, JavaScript, style sheets, etc. within the configuration and voila, you have your own branded site.
The product relies on using your Enterprise LDAP directory, often OpenLDAP, Active Directory, 389 Directory, etc. There are custom schema attributes that the product relies on which you can opt to import into your directory as its own objectClass or you can configure an external database. There is an option for a local database, but I wouldn’t recommend that in a production environment. Modules can be simply enabled and scoped to various LDAP filters allowing for robust flexibility and virtually all text, emails, buttons are configured within the UI. There are also web hooks or LDAP operation hooks within the application so you can configure, so if you need to modify and LDAP attribute after someone changes their password or make a web service call to another system with the users password so it can be synchronized to other applications you can do that.
Below are some screenshots that outline some of the various features I have discussed. If you would like more information or to view a demo please contact us!
Public Modules: A list of various self-service modules that can be enabled. Each having it’s own configurable workflow for which fields to display, what validation checks should be in place and what text you want displayed.
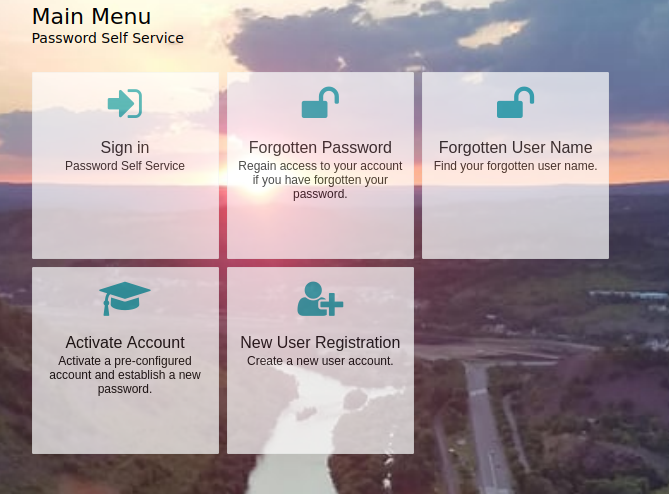
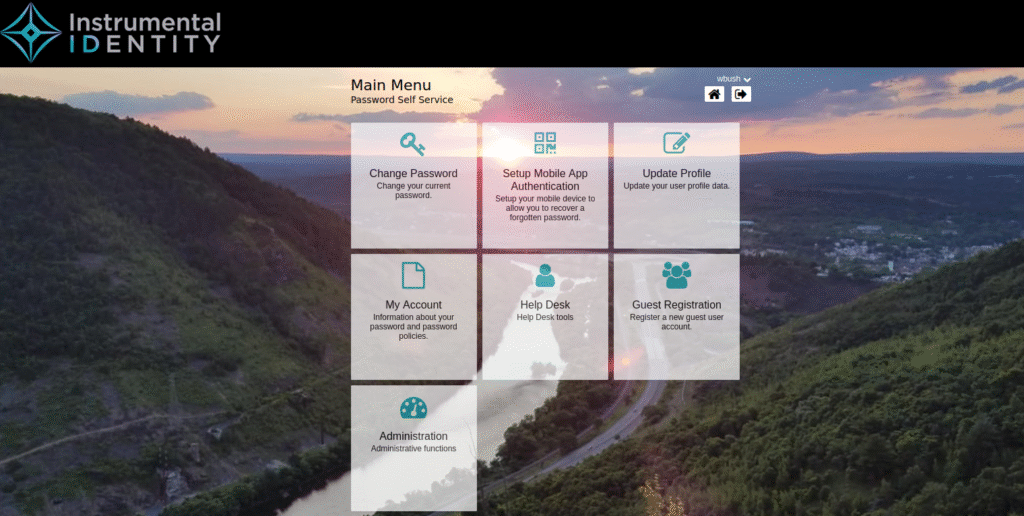
Authenticated Modules: A list of various modules a user may see when they log in. Common ones are change password, Help Desk functionality where your Help Desk can search users, unlock accounts, verify users with an OTP and reset passwords. Here end-users may also be able to update certain fields in LDAP like a phone number for example.
Forgot Password: An example sequence flow for doing self-service password reset when a user has forgotten their password.
(Click the arrow to the right to see each step in the flow.)
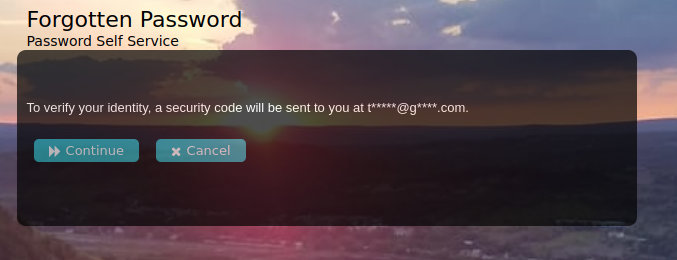
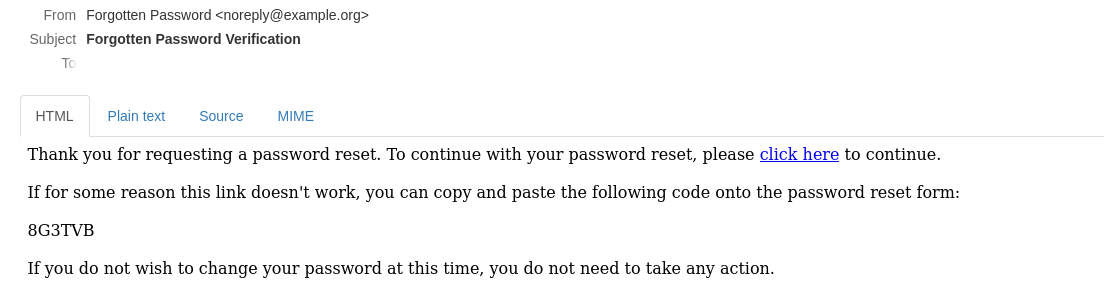
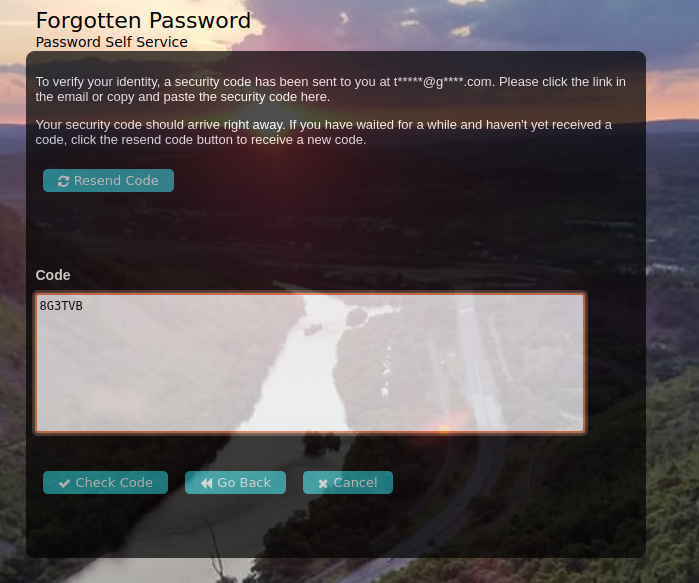
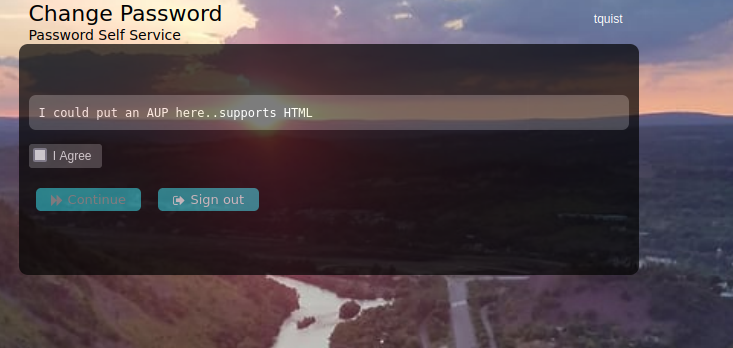
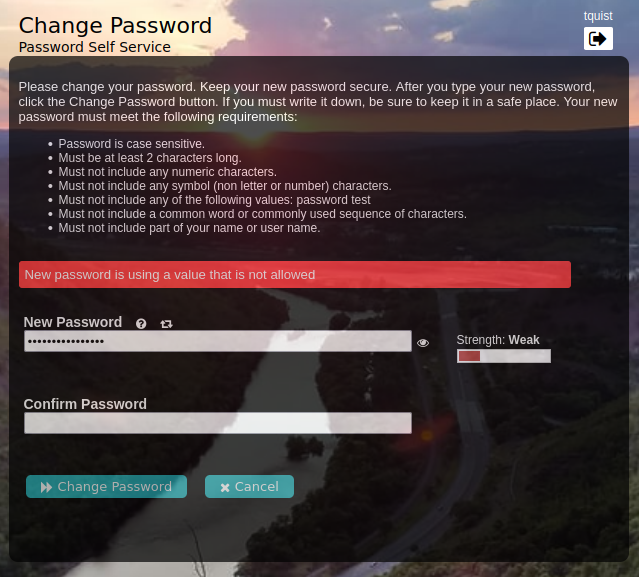
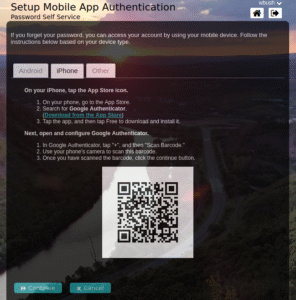
MFA Password Reset: An administrator may want to configure the use of MFA for self-service password reset, or be required in addition to users needing do use an OTP to email or SMS. This can be easily configured and users can use any application that supports TOTP such as Duo, Authenticator, Authy, etc.
Once a user has enrolled their device they can use it to reset their password if they have forgotten it.
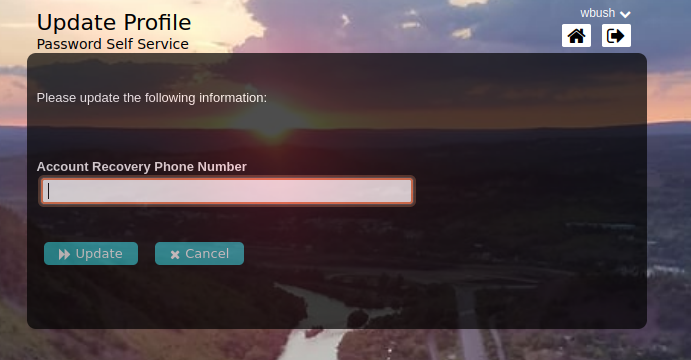
Update Profile: This allows end users to be able to update attributes you want them to in LDAP. You may also inject web hooks in this workflow so other external systems can get updates as well.
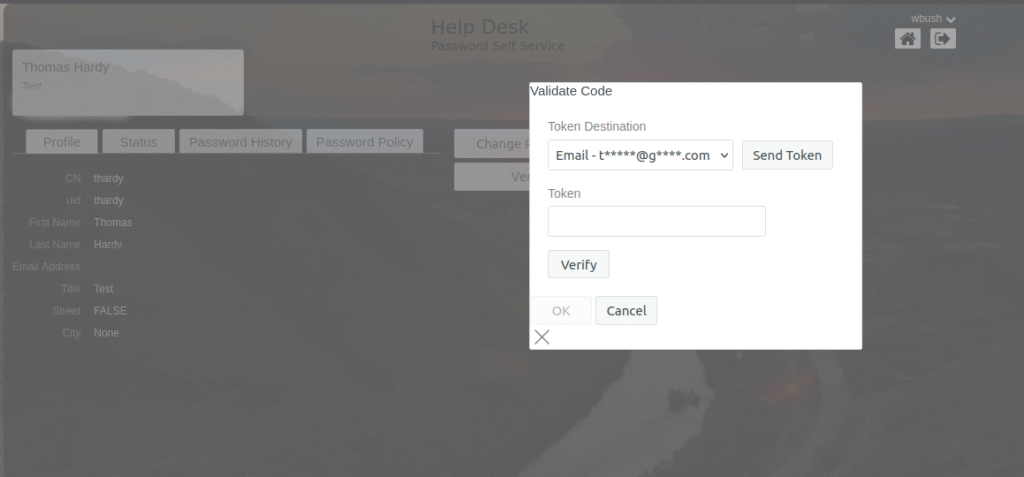
Help Desk Module: Here you can define which users or group of users can do end-user support, including password resets. The screenshot shows how you can require identity verification before the help desk can resetting a password for an end user.
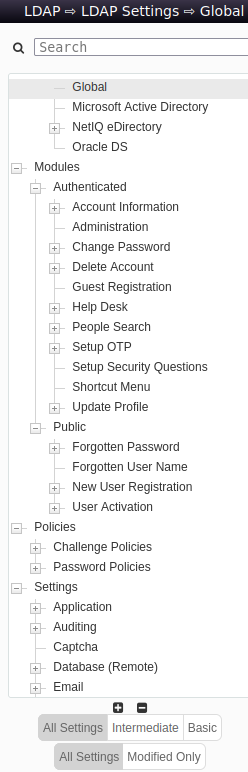
Configuration: As mentioned previously all configuration occurs within the user interface and is very intuitive and easy to navigate.
